This article shows how to implement Elipse E3 applications in environments regulated by FDA standard CFR 21.
1) Overview
About FDA’s standard CFR 21 Part 11
In 1991, members of the pharmaceutical industry met with the United States Food and Drug Administration (FDA) to determine how they could accommodate paperless record systems under the current good manufacturing practice (CGMP) regulations in parts 210 and 211. FDA created a Task Force on Electronic Identification/Signatures to develop a uniform approach by which the agency could accept electronic signatures and records in all program areas.
The final rule provides criteria under which FDA will consider electronic records to be equivalent to paper records, and electronic signatures equivalent to traditional and written signatures. Part 11 (CFR 21 Part 11) applies to any paper records required by statute or agency regulations. It supersedes any existing paper record requirements by providing that electronic records may be used in lieu of paper records. Electronic signatures which meet the requirements of the rule will be considered to be equivalent to full handwritten signatures, initials, and other general signings required by agency regulations.
FDA CFR 21 Part 11 Requirements Summary
The requirements show the need for a secure control system to include user login, automatic logout after no user activity, as well as procedures to ensure that the user performing the actions on the system is the authorized user and not an imposter. A closed system or a runtime only system is a means of securing the control system as it only allows authorized users to access and apply changes to the system.
Another major issue of the requirements involves tracking logged data and system changes. When the signed user makes any changes, the will be able to store the records electronically via password or a suitable biometric device. Logged data must have a valid timestamp and be stored safely. This includes a full audit trail log of any changes that are made to the data along with backup and restore procedures.
About this article
This document works as a guide on how to configure Elipse E3 to meet each requirement of CFR 21 Part 11. You can implement Elipse E3 to meet these requirements. However, it is important to understand that this will not validate Elipse E3, but rather implement the process. Therefore, the system must still undergo the proper FDA validations to meet the requirements, including both documentation and training.
We will explain the guidelines on how to implement Elipse E3 to comply with CFR 21 Part 11 in the following sections. Then, we provide step-by-step instructions for each relevant subpart in sections B and C of the CFR 21 Part 11. Finally, we follow them with a comment made by the Elipse Software staff (signaled as the examples below) and, when applicable, a comment for an implementation guideline.
Standard CFR 21’s text
A text into this fontface (italics) represents a relevant extract from CFR 21 Part 11 document.
A text signaled as follows represents the comments by the Elipse Software teams about the following subjects:
- (Commands) Describes the issuing of operational commands.
- (Data Logging) Refer to logging of data.
- (E3) Describes how to use Elipse E3 for the Server or Viewer consoles.
- (ElipseX) Refers to areas where Elipse E3 libraries (ElipseX) will assist in developing a solution.
- (FDA) Discusses the FDA requirements regarding procedures for obtaining the “CFR 21 Part 11” certification. These requirements do not directly involve the E3 implementation.
- (Security) These sections refer to system security, both Elipse E3 and/or Windows security.
2) FDA CFR 21 Part 11 commented
Subpart B – Electronic Records
§ 11.10 Controls for closed systems.
Persons who use closed systems to create, modify, maintain, or transmit electronic records shall employ procedures and controls designed to ensure the authenticity, integrity, and, when appropriate, the confidentiality of electronic records, and to ensure that the signer cannot readily repudiate the signed record as not genuine. Such procedures and controls shall include the following:
PS: Closed system is an environment in which system access is controlled by persons who are responsible for the content of electronic records that are on the system.
(E3) In order to implement closed systems, we recommend using an E3 Server only copy (with no E3 Studio). We also recommend using Windows security to control access to the application files. It is the customer’s responsibility to ensure there are procedures to control access to the system and its files.
Although one can only edit an Elipse E3 file (PRJ, LIB, etc.) with a specific authorization in the development environment (E3 Studio), by default, these files have no protection against writing. So, whenever possible, you should add protection from accidental edition in PRJ or LIB files. (See next section for protection example inside E3 Studio).
(a) Validation of systems to ensure accuracy, reliability, consistent intended performance, and the ability to discern invalid or altered records.
(FDA) It is the customer’s responsibility to ensure the systems undergo the proper FDA validation procedure.
(b) The ability to generate accurate and complete copies of records in both human readable and electronic form suitable for inspection, review, and copying by the agency. Persons should contact the agency if there are any questions regarding the ability of the agency to perform such review and copying of the electronic records.
(Data Logging) You must log the electronic records to a secure relational database. The application’s developer shall never include routines or SQL statements into an application that could delete or destroy records, but rather add new records for authorized changes . All logged records should include the user’s security identifier and proper security measures. For that, the developer needs to include the field ActorID in the E3 AlarmServer database. As for other Audit Trail information, Elipse E3 will automatically log all operations.
To do so, we suggest using one of the DBMS supported by Elipse E3 (Oracle, SQL Server, PostgreSQL or MySQL). Use the Database security to grant access to application’s database and tables to a single, specific user (via login/password). Store this information inside Elipse E3’s Database Server (in the PRJ files).
We do not recommend using MDB. However, depending on circumstances, you can use it for testing purposes. Then, apply the security user’s and Access’s security directives when in Windows environment.
You must configure human readable reports to display the data logged to the secure relational database, where the FDA can copy it at any time. Use E3 Reports to create the reports you need, exporting data to formats like HTML, PDF and, XLS.
(c) Protection of records to enable their accurate and ready retrieval throughout the records retention period.
(FDA) (E3) Keep the data logged to the secure relational database for the appropriate retention period and protect it via security. You can configure this in Elipse E3 inside AlarmServer, Historic, and Domain configuration dialogs. Alternatively, make sure to use suitable secure backup and restore procedures.
(d) Limiting system access to unauthorized individuals.
(Security) Use Elipse E3’s security settings to restrict users to areas where they have the appropriate authorization level to access. Set up Elipse E3 to log users out after an inactivity period. Make sure to monitor any unsuccessful login.
(e) Use of secure, computer-generated, time-stamped audit trails to independently record the date and time of operator entries and actions that create, modify, or delete electronic records. Record changes shall not obscure previously recorded information. Such audit trail documentation shall be retained for a period at least as long as that required for the subject electronic records and shall be available for agency review and copying.
(Data Logging) All E3 standard data logging operations necessarily include time stamping and never modify or delete records, unless a developer personally overrides this code. However, to do so, the developer will need to generate a specific operation sequence to call a electronic signature, store the operation at the audit trail logs, and inform who was the responsible for doing each task (what, where, and when).
When using multiple stations, use a time broadcast procedure to synchronize all stations clocks.
(f) Use of operational system checks to enforce permitted sequencing of steps and events, as appropriate. The agency advises that the purpose of performing operational checks is to ensure that operations (such as manufacturing production steps and signings to indicate initiation or completion of those steps) are not executed outside of the predefined order established by the operating organization.
(ElipseX) Make sure to configure Elipse E3 to ensure users follow an authorized sequence of steps when operating the system. We recommend using ElipseX objects to ensure users follow the sequence in the entire system.
(g) Use of authority checks to ensure that only authorized individuals can use the system, electronically sign a record, access the operation or computer system input or output device, alter a record, or perform the operation at hand.
(Security) Use Elipse E3’s security settings to restrict users to their appropriate authorization level of access, including operation and data logs. Extra security instructions include:
-
- Set up E3 Viewer to log users out after a certain inactivity time.
- Make sure new passwords have a minimum length.
- Monitor any unsuccessful login.
(h) Use of device (e.g., terminal) checks to determine, as appropriate, the validity of the source of data input or operational instruction.
(Commands) Operational commands must comply with E3 Viewer terminal location and user’s area to check its validity.
(ElipseX) Use ElipseX objects to add an extra layer of safety to these operations.
(i) Determination that persons who develop, maintain, or use electronic record/electronic signature systems have the education, training, and experience to perform their assigned tasks.
(FDA) It is the customer’s responsibility to provide users with the appropriate training to ensure correct system operation.
(j) The establishment of, and adherence to, written policies that hold individuals accountable and responsible for actions initiated under their electronic signatures, in order to deter record and signature falsification.
(FDA) It is the customer’s responsibility to ensure suitable policies are in place to allow the use of electronic signatures by the FDA.
(k) Use of appropriate controls over systems documentation including:
(1) Adequate controls over the distribution of, access to, and use of documentation for system operation and maintenance.
(2) Revision and change control procedures to maintain an audit trail that documents time-sequenced development and modification of systems documentation.
(FDA) Product Manuals are available when installing Elipse E3. Make sure to control all documentation in regards to distribution, access and use. Change control procedures should be in place for system documentation.
§ 11.30 Controls for open systems.
Persons who use open systems to create, modify, maintain, or transmit electronic records shall employ procedures and controls designed to ensure the authenticity, integrity, and, as appropriate, the confidentiality of electronic records from the point of their creation to the point of their receipt.
Such procedures and controls shall include those identified in § 11.10, as appropriate, and additional measures such as document encryption and use of appropriate digital signature standards to ensure, as necessary under the circumstances, record authenticity, integrity, and confidentiality.
(FDA) It is the customer’s responsibility to implement procedures and controls to provide secure applications and data handling in open systems.
§ 11.50 Signature manifestations.
(a) Signed electronic records shall contain information associated with the signing that clearly indicates all of the following:
(1) The printed name of the signer;
(2) The date and time when the signature was executed; and
(3) The meaning (such as review, approval, responsibility, or authorship) associated with the signature.
(b) The items identified in paragraphs (a)(1), (a)(2), and (a)(3) of this section shall be subject to the same controls as for electronic records and shall be included as part of any human readable form of the electronic record (such as electronic display or printout).
(Data Logging) The system requires all logged, audit and other electronic data to contain the actual username, date and time, and the reason for the operation. All these fields already compose part of the audit trail database and electronic signature procedures in Elipse E3. However, make sure to include them as fields in the AlarmServer or any other historic files.
Make sure to set up human readable reports to display the data logged to the secure relational database and make them available for copy by the FDA.
§ 11.70 Signature/record linking.
Electronic signatures and handwritten signatures executed to electronic records shall be linked to their respective electronic records to ensure that the signatures cannot be excised, copied, or otherwise transferred to falsify an electronic record by ordinary means.
(Data Logging) Make sure all logged, audit and other electronic data contain the security identifier or username (if unique) linked to the performed operation. Use Elipse E3’s security settings to restrict users to their appropriate authorization level to access, including operation and data logs.
The agency agrees that the word “link” would offer persons greater flexibility in implementing the intent of this provision and in associating the names of individuals with their identification codes/passwords without actually recording the passwords themselves in electronic records.
Subpart C – Electronic Signatures
§ 11.100 General requirements.
(a) Each electronic signature shall be unique to one individual and shall not be reused by, or reassigned to, anyone else.
(Security) Elipse E3, by default, does not allow password sharing.
(b) Before an organization establishes, assigns, certifies, or otherwise sanctions an individual’s electronic signature, or any element of such electronic signature, the organization shall verify the identity of the individual.
(FDA) It is the customer’s responsibility to ensure that procedures are in place to verify the identity of individuals within the system.
(c) Persons using electronic signatures shall, prior to or at the time of such use, certify to the agency that the electronic signatures in their system, used on or after August 20, 1997, are intended to be the legally binding equivalent of traditional handwritten signatures.
(1) The certification shall be submitted in paper form and signed with a traditional handwritten signature, to the Office of Regional Operations (HFC–100), 5600 Fishers Lane, Rockville, MD 20857.
(2) Persons using electronic signatures shall, upon agency request, provide additional certification or testimony that a specific electronic signature is the legally binding equivalent of the signer’s handwritten signature.
(FDA) It is the customer’s responsibility to ensure systems undergo the proper FDA validation procedure.
§ 11.200 Electronic signature components and controls.
(a) Electronic signatures that are not based upon biometrics shall:
(1) Employ at least two distinct identification components such as an identification code and password.
(i) When an individual executes a series of signings during a single, continuous period of controlled system access, the first signing shall be executed using all electronic signature components; subsequent signings shall be executed using at least one electronic signature component that is only executable by, and designed to be used only by, the individual.
(ii) When an individual executes one or more signings not performed during a single, continuous period of controlled system access, each signing shall be executed using all of the electronic signature components.
(Security) Elise E3’s security must provide a username and password for each user. Users can only gain access to the system via login, with their username and password. Subsequent entries should require only the user’s password (this information pertains only to the user).
Set up Elipse E3 to log a user out after some inactivity time. Make sure users can’t leave the terminal unattended for long periods of time.
(2) Be used only by their genuine owners; and
(3) Be administered and executed to ensure that attempted use of an individual’s electronic signature by anyone other than its genuine owner requires collaboration of two or more individuals.
(b) Electronic signatures based upon biometrics shall be designed to ensure that they cannot be used by anyone other than their genuine owners.
(FDA) It is the customer’s responsibility to ensure that only the owner of the electronic signatures logs in to it. Therefore, Elipse E3 cannot assure that the person typing an username and password is the person thy claim to be.
The agency advises that the intent of the collaboration provision is to require that the components of a non-biometric electronic signature cannot be used by one individual without the prior knowledge of a second individual. One type of situation the agency seeks to prevent is the use of a component such as a card or token that a person may leave unattended. If an individual must collaborate with another individual by disclosing a password, the risks of betrayal and disclosure are greatly increased and this helps to deter such actions.
(FDA) Make sure any attempts to use someone else’s electronic signature will require the joint effort of two or more people. When using biometrics for electronic signatures, make sure only the signature’s owner has access to it.
§ 11.300 Controls for identification codes/passwords.
Persons who use electronic signatures based upon use of identification codes in combination with passwords shall employ controls to ensure their security and integrity. Such controls shall include:
(a) Maintaining the uniqueness of each combined identification code and password, such that no two individuals have the same combination of identification code and password.
(Security) Elipse E3’s standard feature.
(b) Ensuring that identification code and password issuances are periodically checked, recalled, or revised (e.g., to cover such events as password aging).
(Security) Use expiry dates to do so.
(c) Following loss management procedures to electronically deauthorize lost, stolen, missing, or otherwise potentially compromised tokens, cards, and other devices that bear or generate identification code or password information, and to issue temporary or permanent replacements using suitable, rigorous controls.
(FDA) It is the customer’s responsibility to ensure secure handling and control of usernames and passwords.
(d) Use of transaction safeguards to prevent unauthorized use of passwords and/or identification codes, and to detect and report in an immediate and urgent manner any attempts at their unauthorized use to the system security unit, and, as appropriate, to organizational management.
(Security) Monitor ay unsuccessful logins attempts, and inform them to the management.
(e) Initial and periodic testing of devices, such as tokens or cards, that bear or generate identification code or password information to ensure that they function properly and have not been altered in an unauthorized manner.
(FDA) It is the customer’s responsibility to implement procedures to ensure devices function properly and have no alterations.
3) Elipse E3 Implementation Details
Protecting Elipse E3 Project and Library Files
Use this operation to protect application files (PRJ and LIB) from unauthorized access. You can restrict them both for editing (Studio Protection) and/or runtime (Execution Protection).
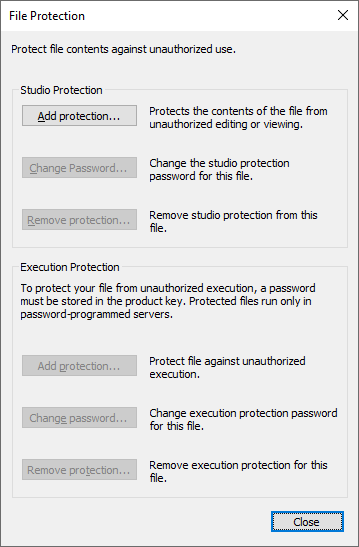
Defining Database Use and Safety
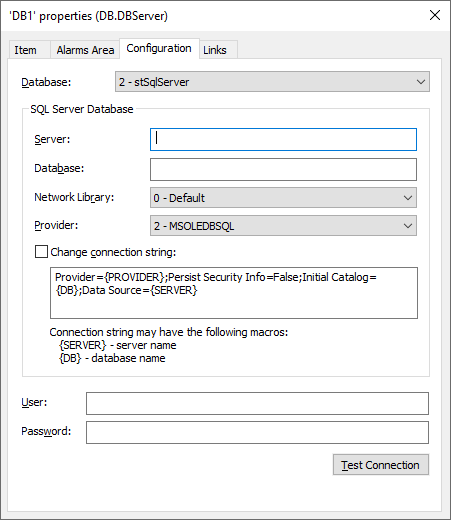
Elipse E3 uses one or more databases to keep all the information and data logging. To do so, configure at least one DBServer in the Domain. Then, connect it to a compatible DBMS (Oracle, SQL Server etc.), with a specific username and login. Inside the database, E3 will store several tables, such as: Alarm, Historian, Formula, User and Audut Trail tables.
Adjusting Table Depth and Backup Politics
While setting up the Historian, Alarm, Storage or Audit Trail, define the table depth and its backup politics, as in the figure below.
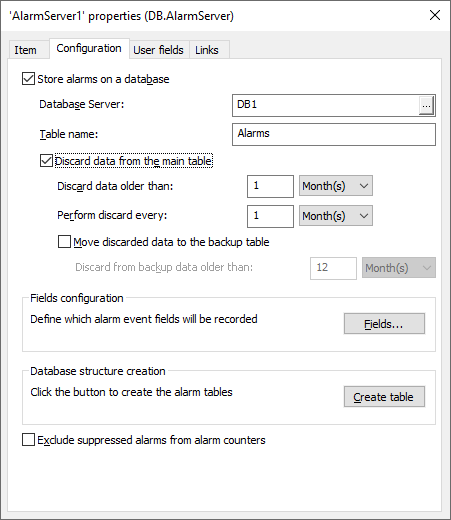 3 – Configuring AlarmServer properties
3 – Configuring AlarmServer properties
Defining Domain Security
According to the directives of standard CFR21, you can define all default security policies for all users. You can set up: account blocking, minimum size, expiration warning, case sensitive passwords, among others. To do so, access E3 Admin, go to Domain Configuration – Properties – Security).
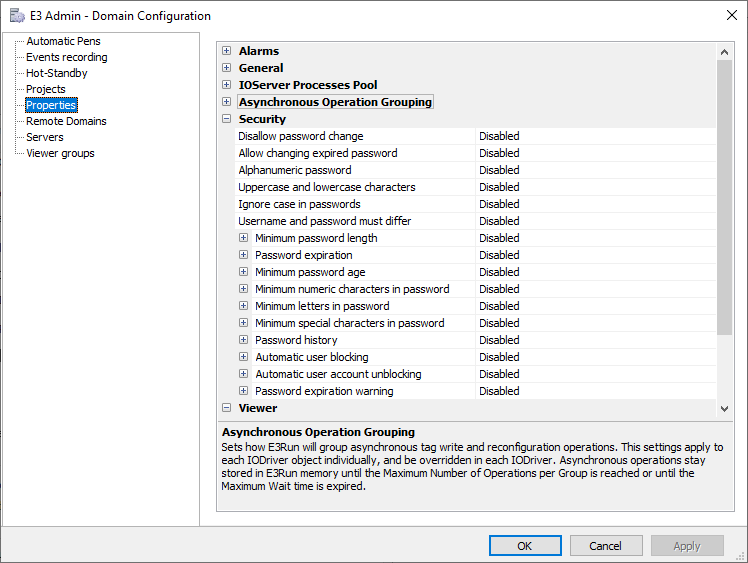 4 – Defining domain security options
4 – Defining domain security optionsCreating Users and Groups
Via Domain – Users option, you can define users and groups for the system. For each user or group you can define or apply security policies, like expiration, account settings, etc.
 5 – Adding a new user
5 – Adding a new user 6 – Setting group policies
6 – Setting group policies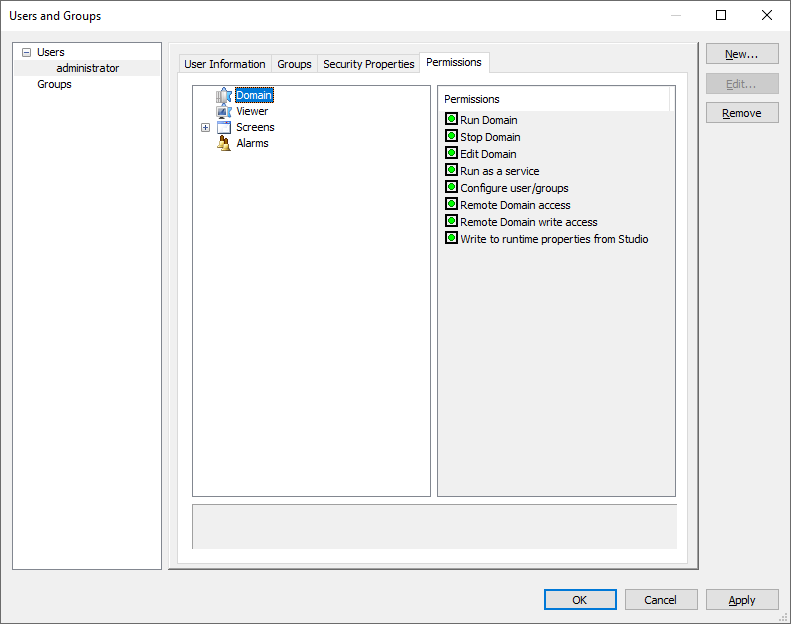 7 – Setting user permissions for domains
7 – Setting user permissions for domains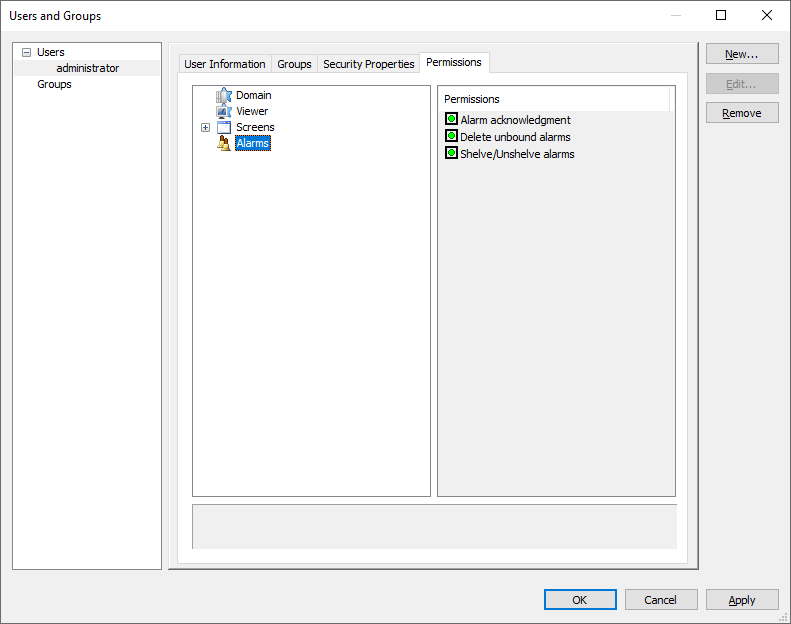 8 – Setting user permissions for alarms
8 – Setting user permissions for alarms
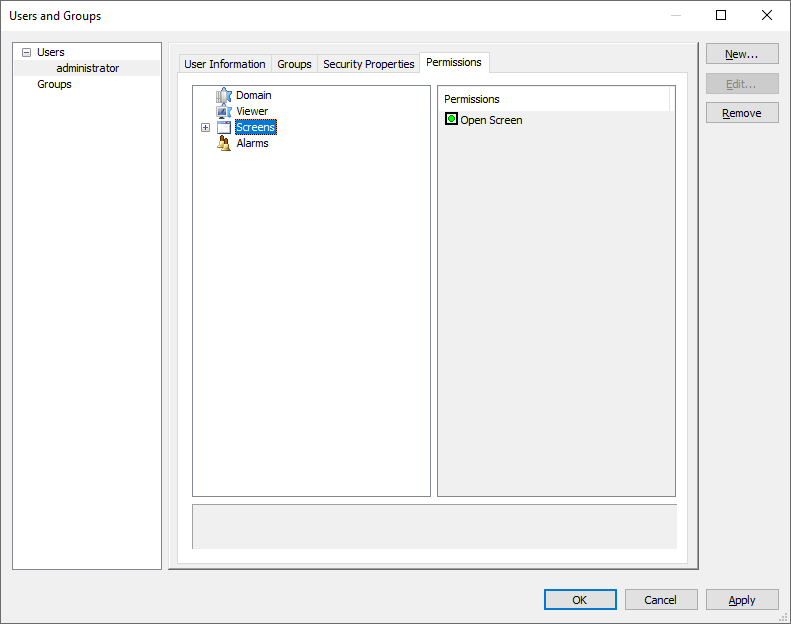 9 – Setting user permissions for screens
9 – Setting user permissions for screens
Defining Audit Trail Configurations and Message Logs
You can define and configure how to record events in the system in Domain Configuration, at Events recording. These events audit the addition, edition, or deletion of users and groups. In addition, they also record data regarding login and logout procedures and their failure, among others. It also records the name of the machine where the event in question took place.
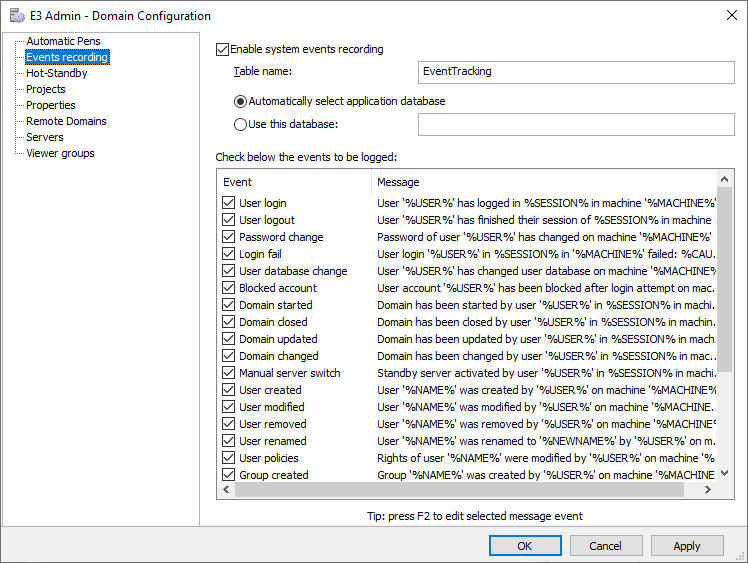 10 – Enabling system events recording
10 – Enabling system events recordingYou can customized these log messages in the Event Editor, as well.
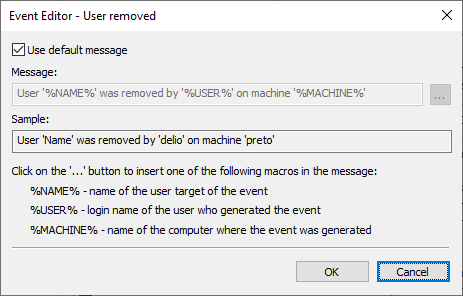 11 – Customizing event messages
11 – Customizing event messages
Electronic Signatures
This window appears whenever the you call the ESign function, allowing for the authentication of specific operations.
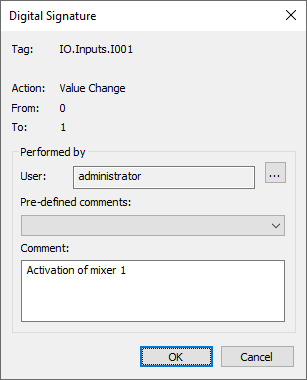 12 – Electronic signature dialog
12 – Electronic signature dialog
ElipseX Examples using ESign and TrackEvent methods
Generic example
If Application.IsUserMemberOfGroup("OPERATORS") Then
If Application.ESign(Param1, Param2,Param3) = True Then
Do_Something
Application.TrackEvent "Tag IO.Inputs.I001 changed to 1"
End If
End If
Writing a value into a tag
Sub Button1_Click()
Dim Tag, User, Comment
Set Tag = Application.GetObject("IO.Inputs.I001")
If Application.ESign(Tag.PathName,, "Value Change", Tag.Value, 1, User, Comment) Then
If Tag.WriteEx 1 Then
Application.TrackEvent "Tag IO.Inputs.I001 changed to 1"
End If
End If
End Sub
Typing directly in a setpoint
Sub Setpoint1_Validate(BOOL Cancel) Dim User, Comment Cancel = Application.ESign (Name, , "Value Change", Tag.Value, 1, User, Comment) If Cancel Then Application.TrackEvent "Tag X changed to " & Value End If End Sub
Inactivity Logout
The inactivity configuration takes place exclusively at the Viewer object. At the Viewer dialog, set the inactivity time (in minutes). To logout the user automatically, you need to insert a small script at the OnInactive event.
Sub Viewer_OnInactive() Logout(0) MsgBox "You were logged of due to inactivity timeout." End Sub
4) Final remarks
We believe that, at this point, Elipse E3 can attend to any kind of process validation predicted at the FDA standard CFR 21 Part 11. Nonetheless, as we release new implementations that can cause impact in the matters of this subject, we will continue to update this document to reflect the state of the art of the history of Elipse E3’s compliance to this FDA standard.
